Create a Google Cloud VPC¶
It's a best practice to create a dedicated network for your new application within your Google Cloud Project. This provides better security, isolation, and control over your network resources.
Step 1: Create the Custom VPC Network¶
- Navigate to the VPC Networks page in the Google Cloud Console within your project: https://console.cloud.google.com/vpc/networks
- Click Create VPC network
Configure VPC Settings¶
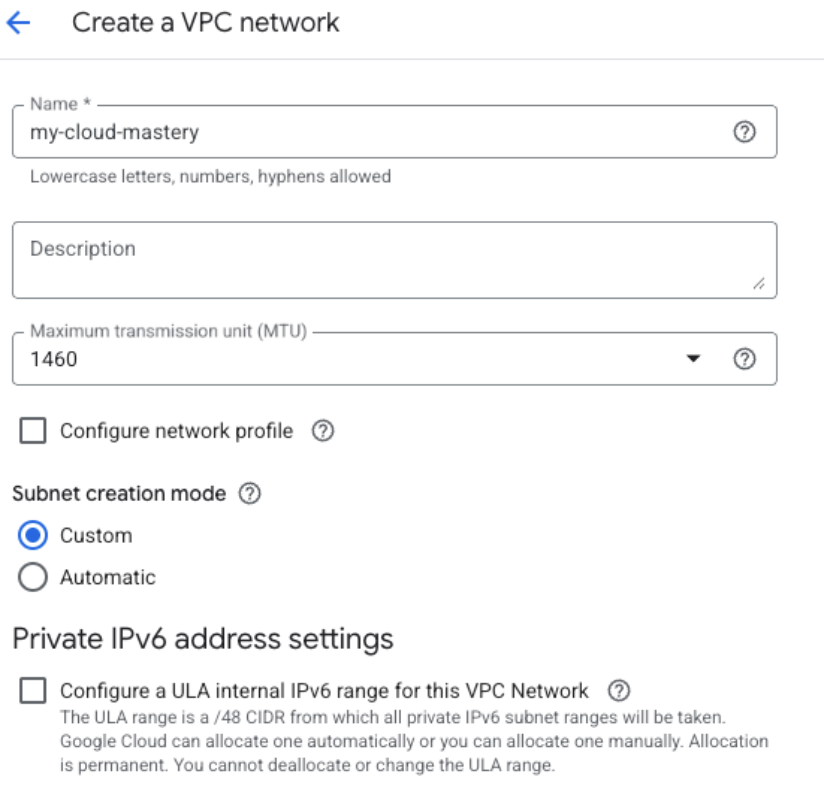
Basic VPC Configuration:
- Name:
my-cloud-mastery-vpc - Description: VPC for migrated application
- Subnet creation mode: Select Custom
Configure Subnet¶
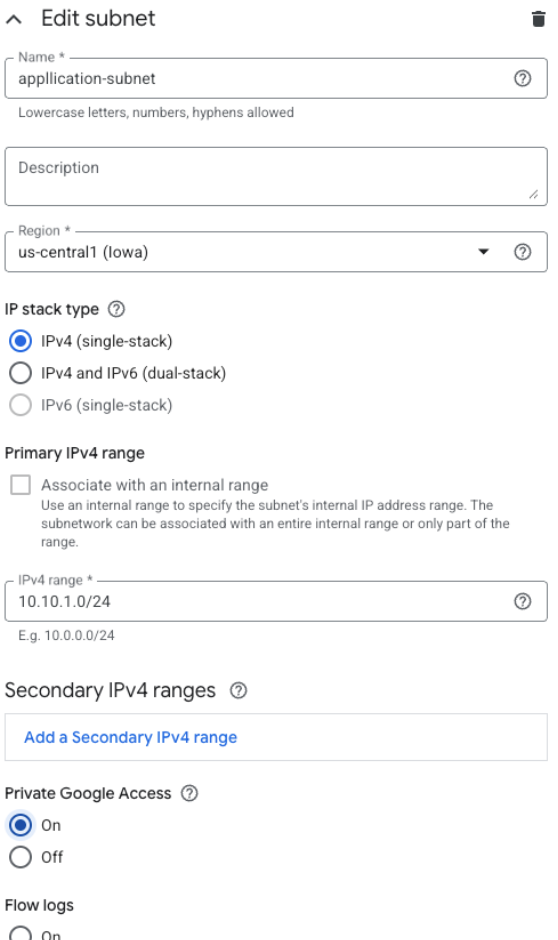
Under New subnet, provide these details:
- Name:
application-subnet - Region: Choose a region where you plan to deploy resources, such as
us-central1 - IP address range: Define a private IP range in CIDR notation
- Recommended:
10.10.1.0/24(This gives you 256 addresses, from 10.10.1.0 to 10.10.1.255)
- Recommended:
- Private Google Access: Turn it On (allows VMs without external IPs to access Google APIs)
- Flow logs: Turn Off (unless you need network monitoring)
- Click DONE to finish subnet configuration
- Click CREATE to create the VPC network
Step 2: Create Firewall Rules¶
Navigate to VPC network → Firewall and create these essential rules for your new VPC network:
Rule 1: Allow SSH Access¶
- Click Create Firewall Rule
- Configure the following settings:
- Name:
allow-ssh-ingress - Description:
Allow SSH access from anywhere - Network:
my-cloud-mastery-vpc - Direction of traffic: Ingress
- Action on match: Allow
- Targets: All instances in the network
- Source filter: IPv4 ranges
- Source IPv4 ranges:
0.0.0.0/0 -
Protocols and ports:
- Check Specified protocols and ports
- Check TCP
- Enter port:
22
-
Click CREATE
Rule 2: Allow HTTP Traffic¶
- Click Create Firewall Rule
- Configure the following settings:
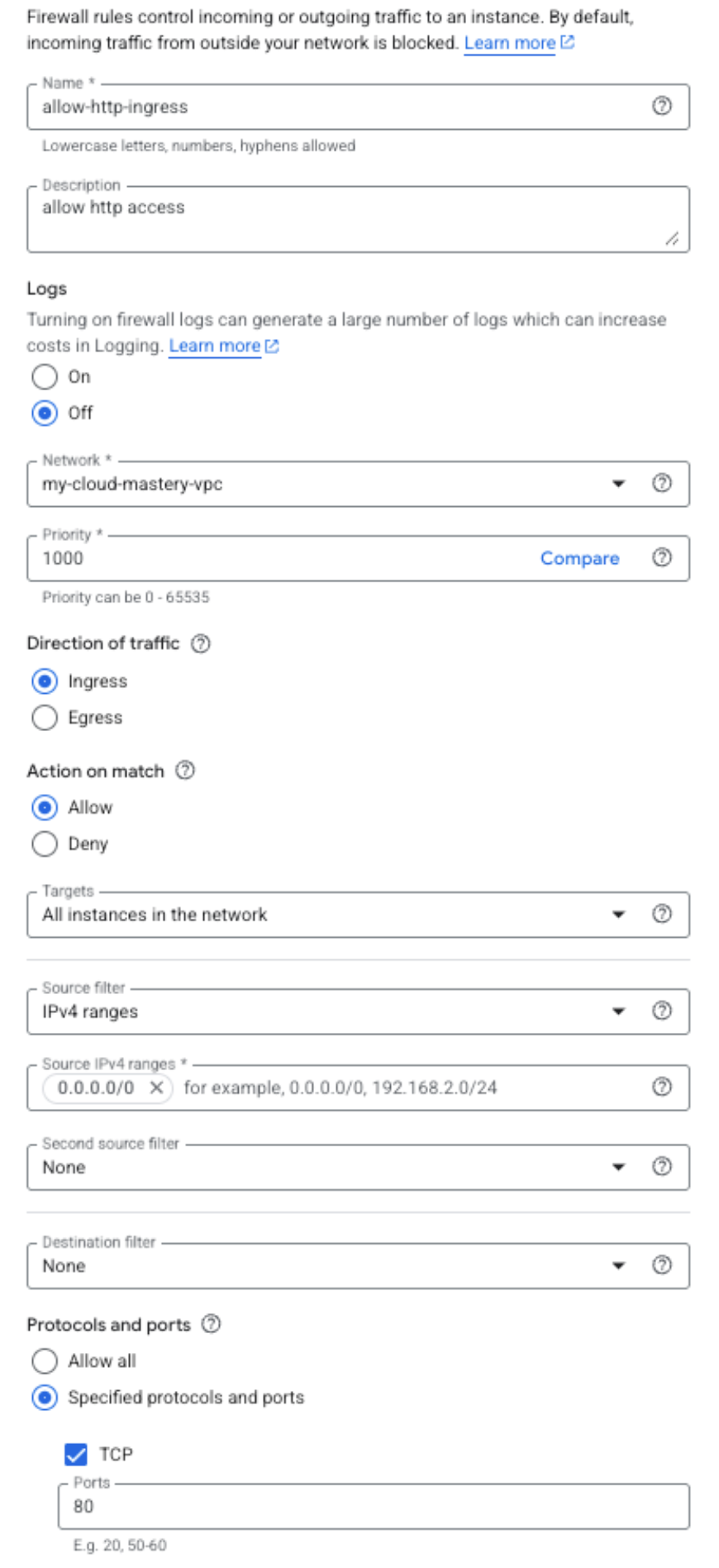
- Name:
allow-http-ingress - Description:
Allow HTTP web traffic from anywhere - Network:
my-cloud-mastery-vpc - Direction of traffic: Ingress
- Action on match: Allow
- Targets: All instances in the network
- Source filter: IPv4 ranges
- Source IPv4 ranges:
0.0.0.0/0(This allows web traffic from anyone on the internet) - Protocols and ports:
- Check Specified protocols and ports
- Check TCP
- Enter port:
80
- Click CREATE
Rule 3: Allow HTTPS Traffic (Optional but Recommended)¶
- Click Create Firewall Rule
- Configure the following settings:
- Name:
allow-https-ingress - Description:
Allow HTTPS web traffic from anywhere - Network:
my-cloud-mastery-vpc - Direction of traffic: Ingress
- Action on match: Allow
- Targets: All instances in the network
- Source filter: IPv4 ranges
- Source IPv4 ranges:
0.0.0.0/0 -
Protocols and ports:
- Check Specified protocols and ports
- Check TCP
- Enter port:
443
-
Click CREATE
Step 3: Verify Your VPC Configuration¶
- Navigate back to VPC networks
- Click on your newly created VPC (
my-cloud-mastery-vpc) - Verify the following:
- Subnets: Your subnet should be listed with the correct IP range
- Firewall rules: All three rules should be associated with your VPC
- Routes: Default routes should be automatically created
Network Architecture Overview¶
Your VPC now provides:
- Isolation: Your migrated application will run in its own network environment
- Security: Controlled access through firewall rules
- Scalability: Room for additional subnets and resources as needed
- Private Google Access: Ability to access Google APIs without external IPs
VPC Setup Complete
Your Google Cloud VPC is now ready to host your migrated virtual machine. The network provides proper isolation and security for your application.
What's Next¶
With your VPC network configured, you're ready to move to Phase 7 where we'll import your VMDK file as a bootable GCP image.